Table of Contents
Tunnelling to Network Devices
Introduction
Tunnelling allows you to securely access any network device as if you were physically on site. You can:
- Reconfigure Cameras remotely (including firmware updates)
- Access and configure routers
- Manage NVRs, DVRs, and other IP Devices
- Troubleshoot network issues
With TetherX, you can achieve this without port forwarding, static IPs, or special software.
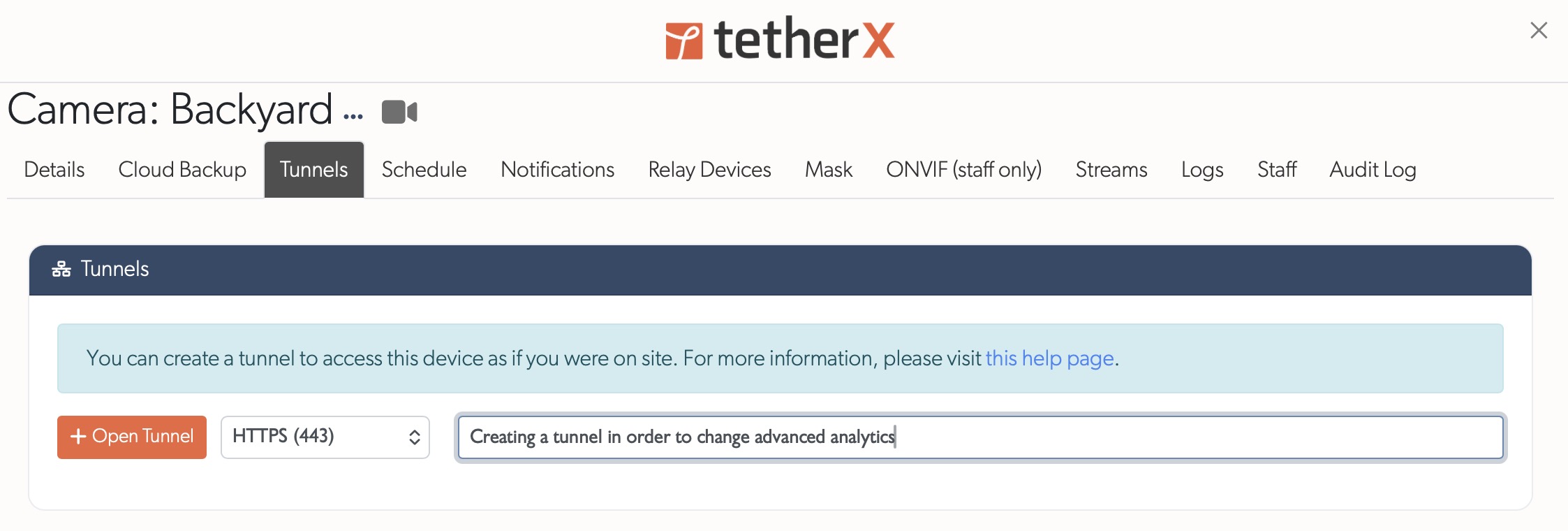
How to Create a Tunnel
- Go to Admin → Devices (or Cameras if tunnelling to a camera)
- Click the name of the device you wish to access
- Click the Tunnels tab
- Select the port (defaults to port 80 for HTTP, 443 for HTTPS) or enter a custom port
- Click Open Tunnel
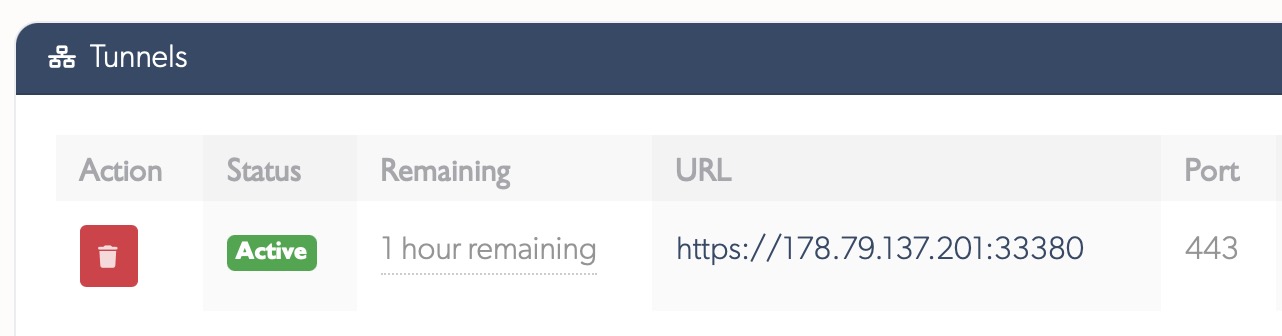
- A secure tunnel URL will appear—click it to access the device directly
Limitations and Considerations
Browser and Plugin Requirements
- Older IP cameras may require ActiveX, Java, Silverlight, or other plugins
- TetherX works with any modern browser without plugins, but certain devices may require Internet Explorer with plugins for full functionality
- Some firmware versions work better with Firefox than Safari/Chrome, and vice versa
Port Requirements
- By default, tunnels connect to port 80 (HTTP) or 443 (HTTPS)
- Some devices require multiple ports for full functionality—consult the device manual or manufacturer
- You can specify a custom port after clicking "Open Tunnel"
Device Requirements
- The device must be online and discoverable on the network
- TetherX must be able to detect the device's MAC address
- The target device must have a web interface enabled
Permissions
To create tunnels, you must have the appropriate permissions:
- Network Management must be enabled on your account
- Integrators must have "Support Access" switched on
- Contact your account administrator if you cannot access this feature
Security
Tunnels provide direct socket access to the device. Encryption depends on the device's protocol: HTTPS and SSH connections are encrypted, whilst HTTP and Telnet connections are not.
Tunnels are temporary and automatically close after 60 minutes, or can be manually closed at any time. No port forwarding or static IP configuration is required.
Referenced in:
